As confirmed in this Microsoft Article: https://support.office.com/en-us/article/access-error-query-is-corrupt-fad205a5-9fd4-49f1-be83-f21636caedec
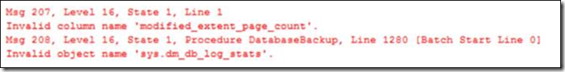
Microsoft Access application users may suddenly start to receive “Error Query ‘’ is corrupt”.
Microsoft released a security update as of November 12th, which can cause the following error in Microsoft Office and Blue Link applications:
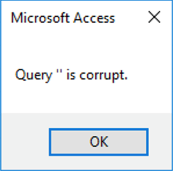
The following KB’s released by Microsoft, are known to cause the issue:
Solution:
Admins who manage WSUS servers should block the three KBs listed above to prevent additional end user machines or servers from receiving these updates.
If you already have these updates installed, and have admin rights to your computer, follow these steps to remove the updates:
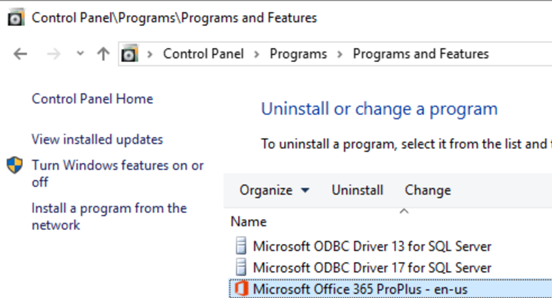
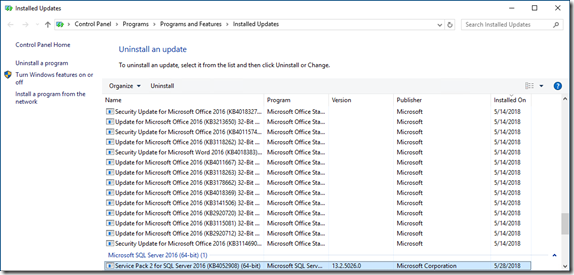
(1) Open Programs & Features
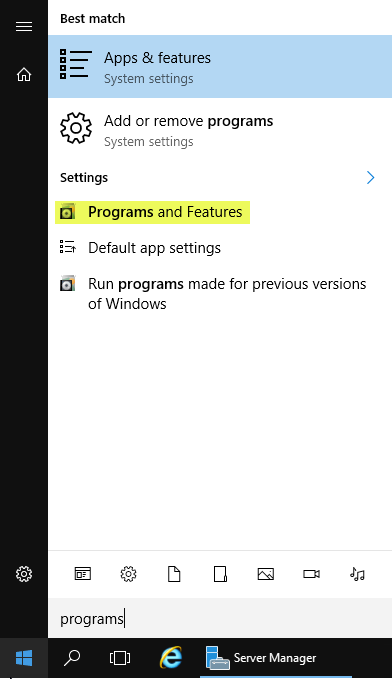
(2) Click on view installed updates.
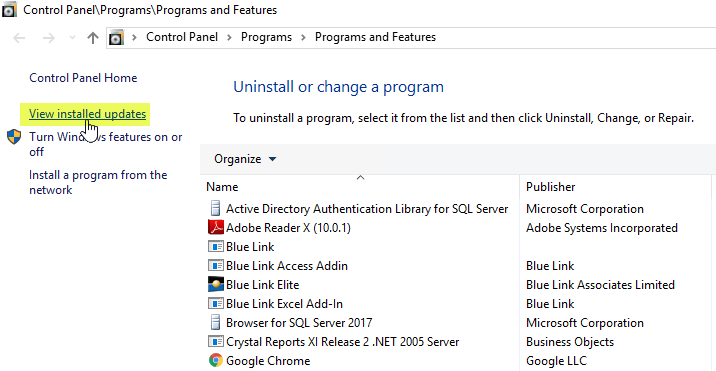
(3) Search for KB KB4484119 & KB4484113
(4) Once you find the update, click on Uninstall update. Please note, this may require a server reboot.
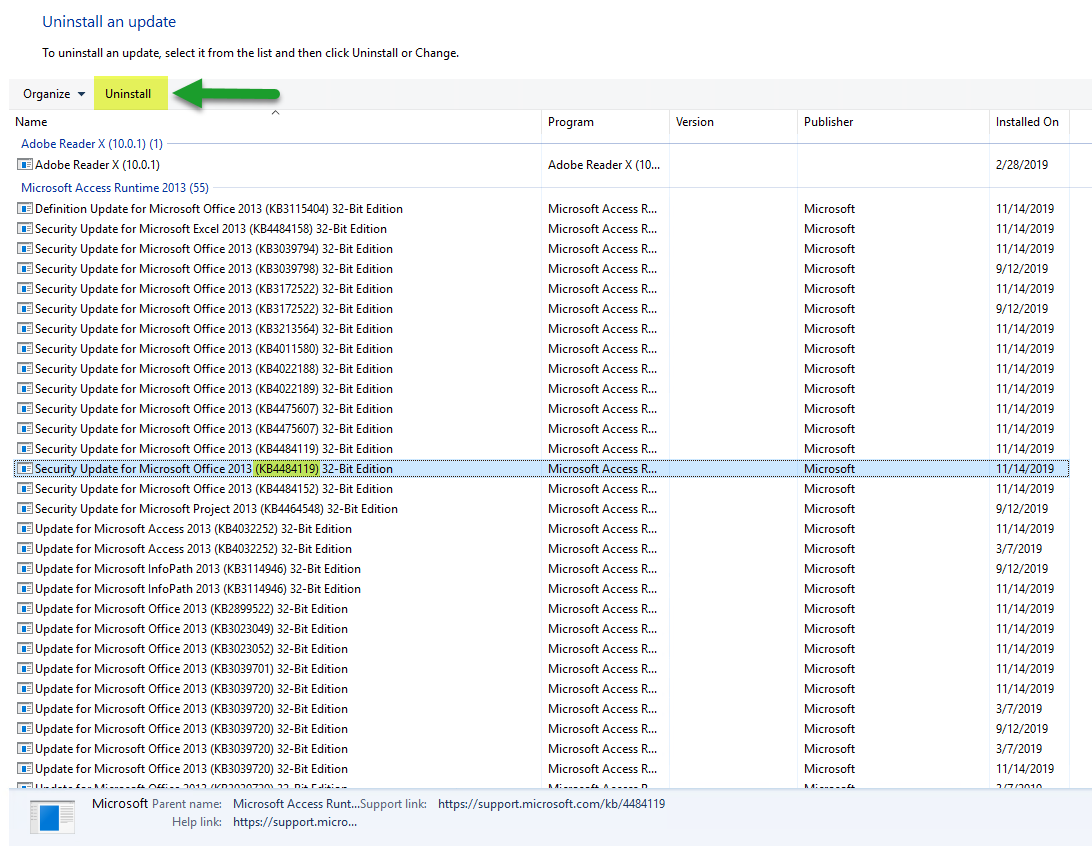
Tip: you can search the list:
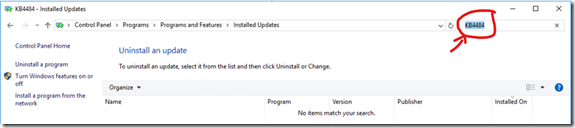
- Tip: To save time, since these KBs all start with “KB4484” searching for that will narrow the list, saving you time.
To Block the update on Windows 10 you now have to download a special tool since Microsoft removed the built-into-the-os version of the feature.
If running Windows 10, you’ll have to download the wushowhide.diagcab file from here:
https://support.microsoft.com/en-us/help/3183922/how-to-temporarily-prevent-a-windows-update-from-reinstalling-in-windo
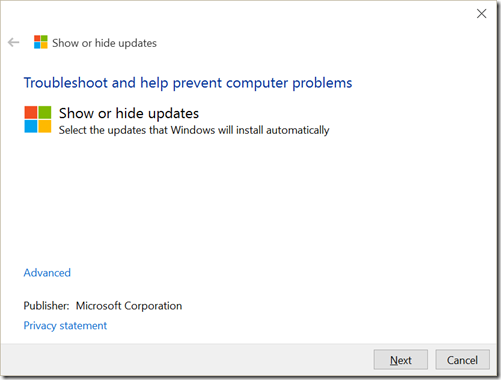
Click Next, To Block the update if already un-installed, choose the hide option and then you’ll be presented with a list of updates that have NOT YET BEEN APPLIED to your machine. If the KB is in this list, you may selected it and then click through the wizard. This will prevent it from being auto-reapplied. (NOTE: This step is not required if you use a WSUS Server and have already blocked the update there).
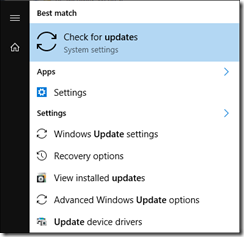
REMEMBER TO CHECK FOR PENDING UPDATES
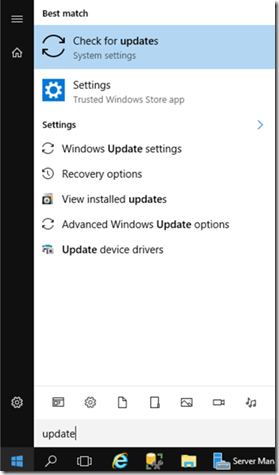
Click Start, Type “Check for Update”
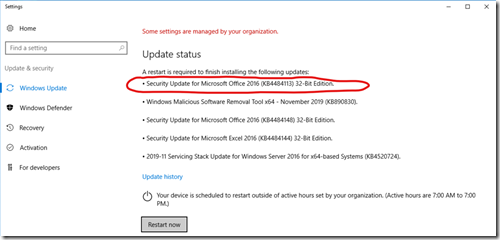
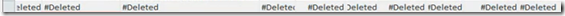
Look at the list of pending updates – if the server has already downloaded and partially installed the update it may show as shown in this screen capture. If it does, the update is already partially installed – it is too late to block it. You must force the server restart and then after the server comes back up, then un-install the update.
Update: 2019-11-17
For servers where the KB update was PENDING (showed in the Updates screen as about to be installed) if actual installation happened on Nov 17th or later it appears not to actually install that KB, but rather installs the updated KB:
https://support.microsoft.com/en-us/help/4484152/security-update-for-office-2013-november-12-2019
In such instance, there is no “un-install” step required.
Access 365 (Office 365)
UPDATE: This issue is also affecting Access 365 (installed via Office 365 with Monthly Channel (Confirmed issue in Build 12130.20344 Click-to-Run).
Apparently, you can force the version of Office to a previous update by following these instructions:
https://support.microsoft.com/en-us/help/2770432/how-to-revert-to-an-earlier-version-of-office-2013-or-office-2016-clic
Here’s how to determine the “previous version” build numbers:
https://docs.microsoft.com/en-us/officeupdates/update-history-office365-proplus-by-date?redirectSourcePath=%252fen-us%252farticle%252fae942449-1fca-4484-898b-a933ea23def7
The previous build (October 30, 2019) is build: 12130.20272.
2019-11-25 – UPDATE: Microsoft has released a patched version 12130.20410 – instructions below are designed to force you to the fixed version, instead of forcing you backwards to the prior version.
To update the app, the Office Deployment Tool (ODT) has to be used. Assuming you extracted it to C:\ODT, then you would update the ODT XML as follows:
|
<Configuration>
<Add SourcePath="C:\odt" OfficeClientEdition="64" Channel="Monthly" >
<Product ID="O365ProPlusRetail">
<Language ID="en-us" />
</Product>
</Add>
<Updates Enabled="TRUE" TargetVersion="16.0.12130.20410" />
<Display Level="Full" AcceptEULA="TRUE" />
<Logging Path="%temp%" />
<Property Name="SharedComputerLicensing" Value="1" />
<Property Name="AUTOACTIVATE" Value="1" />
</Configuration>
|
If you have a C:\ODT\Office folder, delete it.
setup /download MyConfigFile.xml
setup /configure MyConfigFile.xml
For me this worked. All I had to do was kick everyone off the server to allow the update to complete. Minutes later the error was gone.
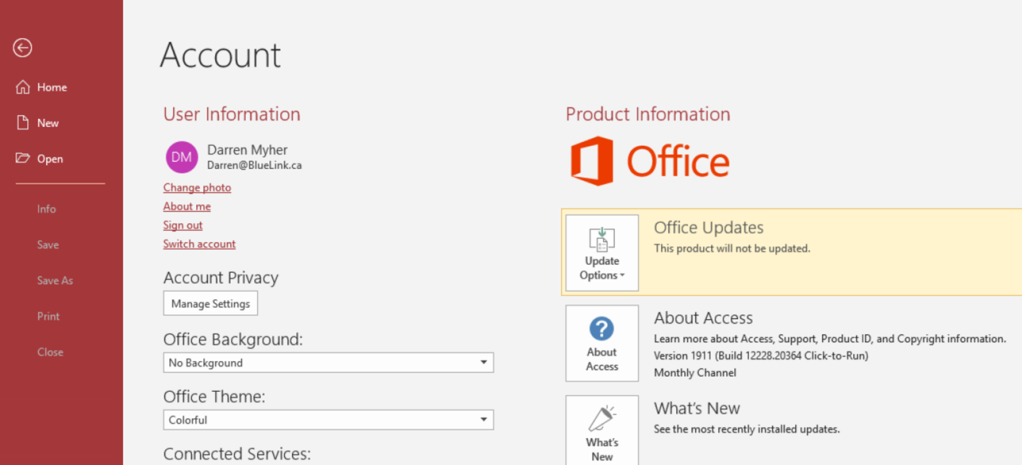
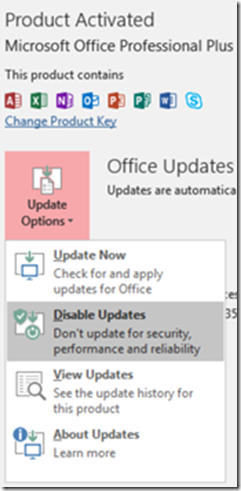
IMPORTANT: After the install completes click File, Account, Update Options then select Disable Updates to prevent the update from just being installed again:
For Access 2019 (Office 2019)
Same as Office 365, except the build numbers are different. In my case, the affected build was Build 10352.20042 Click-to-Run.
Here’s how to determine the “previous version” build numbers:
https://docs.microsoft.com/en-us/officeupdates/update-history-office-2019
Need to the October 8, 2019 build: 10351.20054
|
<Configuration>
<Add OfficeClientEdition="64" Channel="PerpetualVL2019">
<Product ID="ProPlus2019Volume" PIDKEY="XXXXX-XXXXX-XXXXX-XXXXX-XXXXX" >
<Language ID="en-us" />
</Product>
</Add>
< RemoveMSI />
<Updates Enabled="TRUE" TargetVersion="16.0.10351.20054" />
<Display Level="None" AcceptEULA="TRUE" />
<Property Name="AUTOACTIVATE" Value="1" />
</Configuration>
|